Ki Editor - an editor that operates on the AST
KI-Editor is an open-source collaborative writing tool that allows multiple users to work on a document simultaneously, with real-time updates and version control. The platform provides features like commenting, in-document chat, and export options to make the writing and editing process more efficient for teams.
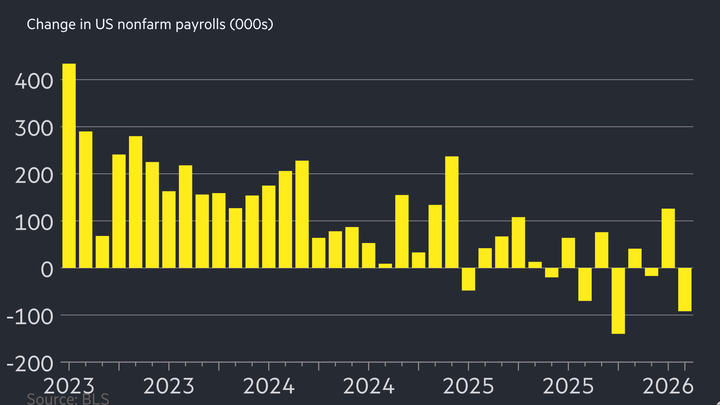
US economy sheds 92,000 jobs in February in sharp slide
The article discusses the rise of large tech companies, known as 'Big Tech', and their growing influence on the global economy, politics, and society. It examines the potential risks and challenges posed by the dominance of these companies, including concerns around privacy, competition, and the concentration of power.

The yoghurt delivery women combatting loneliness in Japan
The article explores how a group of women in Japan are combating loneliness in their communities by delivering yogurt to elderly residents, providing not just a daily food delivery but also a social connection and a way to check on the well-being of the elderly.

The Millisecond That Could Change Cancer Treatment
The article discusses the development of a new form of radiotherapy that uses ultrashort pulses of high-energy electrons to treat cancer tumors more precisely and with less collateral damage to surrounding healthy tissue compared to traditional radiation therapy.

PC processors entered the Gigahertz era today in the year 2000 with AMD's Athlon
In the year 2000, AMD's Athlon processor became the first consumer PC CPU to reach 1 GHz, marking the dawn of the gigahertz era in personal computing. AMD's marketing of the 1 GHz Athlon as a breakthrough achievement helped the company gain ground on industry leader Intel.

Tinnitus Is Connected to Sleep
The article explores a potential connection between tinnitus, a common hearing condition characterized by ringing in the ears, and a crucial bodily function. Researchers suggest that tinnitus may be linked to the body's regulation of carbon dioxide levels, providing new insights into the underlying mechanisms of this persistent condition.

Filesystems Are Having a Moment
This article explores the importance of file systems in modern computing, highlighting their role in data storage, organization, and management. It discusses the evolution of file systems and the growing interest in understanding their impact on system performance and user experience.
Boy I was wrong about the Fediverse
The article discusses the author's changing perspective on the Fediverse, a decentralized social media network. It explores the benefits and challenges of the Fediverse, highlighting its potential as an alternative to traditional social media platforms.
Show HN: ANSI-Saver – A macOS Screensaver
Hi, I've been working on something I've been thinking for long time but since I had no experience with macOS screen savers I always posponed. Now thanks to Claude I was able to create a screensaver that scroll ANSI files while your computer is idle.
It allow to use local ANS files or packs directly from 16colo.rs.
Repo: https://github.com/lardissone/ansi-saver

We're Training Students to Write Worse to Prove They're Not Robots
The article discusses how AI-powered writing tools and services are becoming more common in schools, leading to concerns that students are being trained to write worse in order to avoid being identified as AI-generated content, which could ultimately push them to rely more on AI assistance.
The Banality of Surveillance
The article discusses the normalization of surveillance in modern society, highlighting how ubiquitous and accepted it has become despite its potential infringement on privacy and civil liberties. It examines how the expansion of surveillance technologies and data collection has become a banal, everyday occurrence that many people have grown accustomed to without much resistance.
War Prediction Markets Are a National-Security Threat
The article discusses the risks of insider trading in the prediction market Polymarket, which could have serious consequences for users. It highlights the need for stronger regulation and oversight to protect investors from potential harm.
The Case of the Disappearing Secretary
This article explores the mysterious disappearance of the former UK Prime Minister Boris Johnson's private secretary, Dominic Cummings, and the potential political implications of this event. It examines the circumstances surrounding Cummings' departure and the ongoing speculation and debate surrounding the matter.

Tech jobs are getting demolished in ways not seen since 2008
The article discusses how the tech industry has experienced significant job losses in recent years, with the Great Recession and the dot-com era contributing to a decline in tech employment. The author suggests that the tech sector may face further job cuts in the coming years, potentially leading to a larger downturn in the industry.
CasNum
The article discusses CasNum, a command-line tool that allows users to quickly and easily convert between different number systems, including decimal, hexadecimal, binary, and more. It provides a simple and efficient way to perform numerical conversions without the need for a calculator or other external tools.

Senators Launch Effort Ban Elected Officials Profiting from Prediction Markets
Senators Merkley and Klobuchar are launching an effort to ban federal elected officials from profiting from prediction markets, which they argue poses conflicts of interest and undermines public trust in government.
Nippon Life Sues OpenAI over Legal Advice to Ex-Beneficiary
The article discusses Japan's efforts to promote renewable energy, with a focus on the government's goal of achieving carbon neutrality by 2050. It highlights the country's progress in expanding its renewable energy capacity, particularly in the solar and offshore wind power sectors.

Sam Altman's greed and dishonesty are finally catching up to him
This article criticizes Sam Altman, the CEO of OpenAI, for his perceived greed and dishonesty in promoting the company's artificial intelligence technology while downplaying its potential risks and limitations.
The One-Person Stack
The article explores the concept of the 'one-person stack', where a single individual manages and maintains a complete technology stack. It discusses the advantages, challenges, and considerations for those who choose to take on this approach to software development and IT management.

Uber CEO on culture: expects weekend email replies, will push out non-performers
The article discusses Uber CEO Dara Khosrowshahi's rejection of the concept of work-life balance, encouraging employees to respond to emails on weekends. This approach has received mixed reactions from Uber's staff, with some expressing concerns about the impact on their personal lives.