Show HN: Remotely use my guitar tuner
Show HN: I Was Here – Draw on street view, others can find your drawings
Hey HN, I made a site where you can draw on street-level panoramas. Your drawings persist and other people can see them in real time.
Strokes get projected onto the 3D panorama so they wrap around buildings and follow the geometry, not just a flat overlay. Uses WebGL2 for rendering, Mapillary for the street imagery.
The idea is for it to become a global canvas, anyone can leave a mark anywhere and others stumble onto it.
Show HN: DenchClaw – Local CRM on Top of OpenClaw
Hi everyone, I am Kumar, co-founder of Dench (https://denchclaw.com). We were part of YC S24, an agentic workflow company that previously worked with sales floors automating niche enterprise tasks such as outbound calling, legal intake, etc.
Building consumer / power-user software always gave me more joy than FDEing into an enterprise. It did not give me joy to manually add AI tools to a cloud harness for every small new thing, at least not as much as completely local software that is open source and has all the powers of OpenClaw (I can now talk to my CRM on Telegram!).
A week ago, we launched Ironclaw, an Open Source OpenClaw CRM Framework (https://x.com/garrytan/status/2023518514120937672?s=20) but people confused us with NearAI’s Ironclaw, so we changed our name to DenchClaw (https://denchclaw.com).
OpenClaw today feels like early React: the primitive is incredibly powerful, but the patterns are still forming, and everyone is piecing together their own way to actually use it. What made React explode was the emergence of frameworks like Gatsby and Next.js that turned raw capability into something opinionated, repeatable, and easy to adopt.
That is how we think about DenchClaw. We are trying to make it one of the clearest, most practical, and most complete ways to use OpenClaw in the real world.
Demo: https://www.youtube.com/watch?v=pfACTbc3Bh4#t=43
npx denchclaw
On Dench, everything sits in a file system, the table filters, views, column toggles, calendar/gantt views, etc, so OpenClaw can directly work with it using Dench’s CRM skill.
The CRM is built on top of DuckDB, the smallest, most performant and at the same time also feature rich database we could find. Thank you DuckDB team!
It creates a new OpenClaw profile called “dench”, and opens a new OpenClaw Gateway… that means you can run all your usual openclaw commands by just prefixing every command with `openclaw --profile dench` . It will start your gateway on port 19001 range. You will be able to access the DenchClaw frontend at localhost:3100. Once you open it on Safari, just add it to your Dock to use it as a PWA.
Think of it as Cursor for your Mac (also works on Linux and Windows) which is based on OpenClaw. DenchClaw has a file tree view for you to use it as an elevated finder tool to do anything on your mac. I use it to create slides, do linkedin outreach using MY browser.
DenchClaw finds your Chrome Profile and copies it fully into its own, so you won’t have to log in into all your websites again. DenchClaw sees what you see, does what you do. It’s an everything app, that sits locally on your mac.
Just ask it “hey import my notion”, “hey import everything from my hubspot”, and it will literally go into your browser, export all objects and documents and put it in its own workspace that you can use.
We would love you all to break it, stress test its CRM capabilities, how it streams subagents for lead enrichment, hook it into your Apollo, Gmail, Notion and everything there is. Looking forward to comments/feedback!
Show HN: The Mog Programming Language
Hi, Ted here, creator of Mog.
- Mog is a statically typed, compiled, embedded language (think statically typed Lua) designed to be written by LLMs -- the full spec fits in 3,200 tokens. - An AI agent writes a Mog program, compiles it, and dynamically loads it as a plugin, script, or hook. - The host controls exactly which functions a Mog program can call (capability-based permissions), so permissions propagate from agent to agent-written code. - Compiled to native code for low-latency plugin execution -- no interpreter overhead, no JIT, no process startup cost. - The compiler is written in safe Rust so the entire toolchain can be audited for security. Even without a full security audit, Mog is already useful for agents extending themselves with their own code. - MIT licensed, contributions welcome.
Motivations for Mog:
1. Syntax Only an AI Could Love: Mog is written for AIs to write, so the spec fits easily in context (~3200 tokens), and it's intended to minimize foot-guns to lower the error rate when generating Mog code. This is why Mog has no operator precedence: non-associative operations have to use parentheses, e.g. (a + b) * c. It's also why there's no implicit type coercion, which I've found over the decades to be an annoying source of runtime bugs. There's also less support in Mog for generics, and there's absolutely no support for metaprogramming, macros, or syntactic abstraction.
When asking people to write code in a language, these restrictions could be onerous. But LLMs don't care, and the less expressivity you trust them with, the better.
2. Capabilities-Based Permissionsl: There's a paradox with existing security models for AI agents. If you give an agent like OpenClaw unfettered access to your data, that's insecure and you'll get pwned. But if you sandbox it, it can't do most of what you want. Worse, if you run scripts the agent wrote, those scripts don't inherit the permissions that constrain the agent's own bash tool calls, which leads to pwnage and other chaos. And that's not even assuming you run one of the many OpenClaw plugins with malware.
Mog tries to solve this by taking inspiration from embedded languages. It compiles all the way to machine code, ahead of time, but the compiler doesn't output any dangerous code (at least it shouldn't -- Mog is quite new, so that could still be buggy). This allows a host program, such as an AI agent, to generate Mog source code, compile it, and load it into itself using dlopen(), while maintaining security guarantees.
The main trick is that a Mog program on its own can't do much. It has no direct access to syscalls, libc, or memory. It can basically call functions, do heap allocations (but only within the arena the host gives it), and return something. If the host wants the Mog program to be able to do I/O, it has to supply the functions that the Mog program will call. A core invariant is that a Mog program should never be able to crash the host program, corrupt its state, or consume more resources than the host allows.
This allows the host to inspect the arguments to any potentially dangerous operation that the Mog program attempts, since it's code that runs in the host. For example, a host agent could give a Mog program a function to run a bash command, then enforce its own session-level permissions on that command, even though the command was dynamically generated by a plugin that was written without prior knowledge of those permission settings.
(There are a couple other tricks that PL people might find interesting. One is that the host can limit the execution time of the guest program. It does this using cooperative interrupt polling, i.e. the compiler inserts runtime checks that check if the host has asked the guest to stop. This causes a roughly 10% drop in performance on extremely tight loops, which are the worst case. It could almost certainly be optimized.)
3. Self Modification Without Restart: When I try to modify my OpenClaw from my phone, I have to restart the whole agent. Mog fixes this: an agent can compile and run new plugins without interrupting a session, which makes it dynamically responsive to user feedback (e.g., you tell it to always ask you before deleting a file and without any interruption it compiles and loads the code to... actually do that).
Async support is built into the language, by adapting LLVM's coroutine lowering to our Rust port of the QBE compiler, which is what Mog uses for compilation. The Mog host library can be slotted into an async event loop (tested with Bun), so Mog async calls get scheduled seamlessly by the agent's event loop. Another trick is that the Mog program uses a stack inside the memory arena that the host provides for it to run in, rather than the system stack. The system tracks a guard page between the stack and heap. This design prevents stack overflow without runtime overhead.
Lots of work still needs to be done to make Mog a "batteries-included" experience like Python. Most of that work involves fleshing out a standard library to include things like JSON, CSV, Sqlite, and HTTP. One high-impact addition would be an `llm` library that allows the guest to make LLM calls through the agent, which should support multiple models and token budgeting, so the host could prevent the plugin from burning too many tokens.
I suspect we'll also want to do more work to make the program lifecycle operations more ergonomic. And finally, there should be a more fully featured library for integrating a Mog host into an AI agent like OpenClaw or OpenAI's Codex CLI.
Show HN: Latchup – Competitive programming for hardware description languages
Latchup is an app that helps users manage their wedding planning tasks and connect with vendors. It offers features such as to-do lists, vendor directories, and communication tools to streamline the wedding planning process.
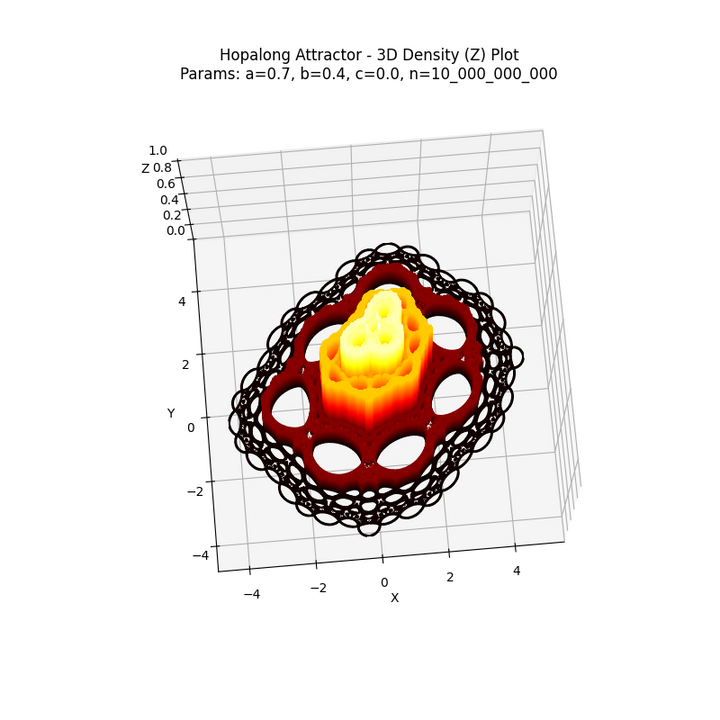
Show HN: Hopalong Attractor. An old classic with a new perspective in 3D
This article introduces the Hopalong fractal, a visually stunning mathematical attractor, and provides a Python implementation for generating and visualizing it. The article explains the mathematical principles behind the Hopalong fractal and includes example code to help readers explore and experiment with this fascinating fractal.
Show HN: VS Code Agent Kanban: Task Management for the AI-Assisted Developer
Agent Kanban has 4 main features:
GitOps & team friendly kanban board integration inside VS Code Structured plan / todo / implement via @kanban commands Leverages your existing agent harness rather than trying to bundle a built in one .md task format provides a permanent (editable) source of truth including considerations, decisions and actions, that is resistant to context rot
Show HN: sAT Protocol – static social networking
Show HN: Skir – like Protocol Buffer but better
Why I built Skir: https://medium.com/@gepheum/i-spent-15-years-with-protobuf-t...
Quick start: npx skir init
All the config lives in one YML file.
Website: https://skir.build
GitHub: https://github.com/gepheum/skir
Would love feedback especially from teams running mixed-language stacks.
Show HN: I built a real-time OSINT dashboard pulling 15 live global feeds
Sup HN,
So I got tired of bouncing between Flightradar, MarineTraffic, and Twitter every time something kicked off globally, so I wrote a dashboard to aggregate it all locally. It’s called Shadowbroker.
I’ll admit I leaned way too hard into the "movie hacker" aesthetic for the UI, but the actual pipeline underneath is real. It pulls commercial/military ADS-B, the AIS WebSocket stream (about 25,000+ ships), N2YO satellite telemetry, and GDELT conflict data into a single MapLibre instance.
Getting this to run without melting my browser was the hardest part. I'm running this on a laptop with an i5 and an RTX 3050, and initially, dumping 30k+ moving GeoJSON features onto the map just crashed everything. I ended up having to write pretty aggressive viewport culling, debounce the state updates, and compress the FastAPI payloads by like 90% just to make it usable.
My favorite part is the signal layer—it actually calculates live GPS jamming zones by aggregating the real-time navigation degradation (NAC-P) of commercial flights overhead.
It’s Next.js and Python. I threw a quick-start script in the releases if you just want to spin it up, but the repo is open if you want to dig into the backend.
Let me know if my MapLibre implementation is terrible, I'm always looking for ways to optimize the rendering.

Show HN: I built a site where strangers leave kind voice notes for each other
Show HN: Zenòdot – Find if a book has been translated into your language
I'm a multilingual reader (Catalan/Spanish/English/Italian), and I kept hitting the same wall: I'd hear about a book and have no way to know if it existed in my language. Turns out this is a genuinely unsolved problem. There's no single database that tracks which books have been translated into which languages. ISBN registries are fragmented by country. Open Library has great English coverage but gaps elsewhere. Wikidata has surprisingly rich translation data but it's locked behind SPARQL. Google Books is inconsistent across regions.
So I built Zenòdot to cross all four and piece the picture together.
What I found building it:
-The ISBN system is far more broken than I expected. ISBNdb has millions of English records but almost nothing for languages like Basque, Icelandic, or Bengali. Books exist in these languages, they just don't exist in the databases.
-Wikidata was the biggest surprise. It has structured translation data for thousands of works, but extracting it requires SPARQL queries, title resolution across scripts (try matching a book title in Chinese to its English original), and author alias caching. Hard to build, but the results fill gaps that no other source covers.
-The most interesting output isn't what the tool finds; it's what it doesn't find. When someone searches for a book in a language and there's no result, that's a demand signal. "Someone in the world wanted this translation and it doesn't exist." That data could be genuinely useful to publishers.
The tool prioritizes your selected languages, so it shows you editions relevant to you first. The philosophy is "documentary infrastructure”: no recommendations, no social features, no accounts. You search, you find (or don't), you go buy the book wherever you want.
Stack: Next.js 15 (App Router), Supabase, Vercel, TypeScript. Solo project, no funding, about 4 months of work.
If you're multilingual or learning a language, I'd especially love your feedback. Try searching for a book you love and switching between languages, that's where the tool shows its value.
Show HN: ChatJC – chatbot for resume/LinkedIn/portfolio info
The article provides an overview of Joshua Curry, a software engineer and technical writer. It highlights his expertise in various programming languages, his contributions to open-source projects, and his experience in the tech industry.
Show HN: Husky hook that blocks Git push until you do your pushups
Show HN: Eyot, A programming language where the GPU is just another thread
Cowleyforniastudios announces the launch of Eyot, a new virtual reality game that allows players to explore a mysterious island and uncover its secrets. The game promises immersive gameplay, stunning visuals, and a compelling narrative.
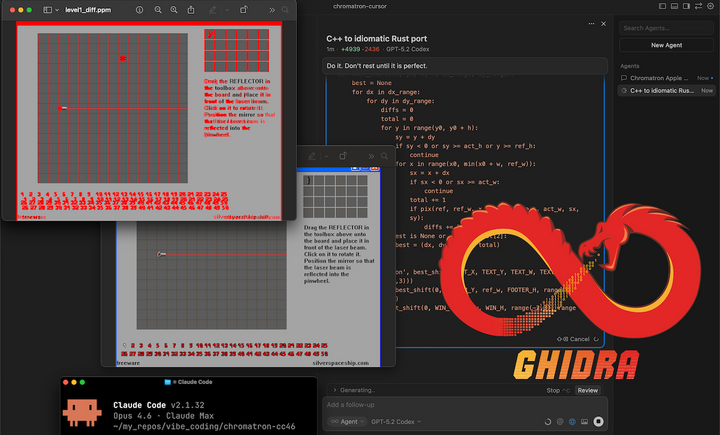
Show HN: Reviving a 20-year-old puzzle game Chromatron with Ghidra and AI
Play: https://p.migdal.pl/chromatron-oxide/ Repo: https://github.com/stared/chromatron-oxide/ (educational purpose only) The original: https://www.silverspaceship.com/chromatron/
Full story in the blog post.

Show HN: Curiosity – DIY 6" Newtonian Reflector Telescope
A DIY Newtonian reflector telescope with dobsonian mount. A fun to do hobby project taking us closer to the moon and beyond. A lot of plans ahead on how to make it much better and portable but this was the first time me and my friend implemented or rather built a telescope.
Have a look at what all we have captured.
Show HN: WolfStack – Proxmox-like server management in a single Rust binary
Wolfscale.org is a website that provides information about the wolves of North America, including their biology, behavior, and conservation efforts. The site covers topics such as wolf ecology, pack dynamics, and the role of wolves in their ecosystems.

Show HN: DopaLoop – Habit tracker for ADHD brains, local-first, no streaks
I got diagnosed with ADHD at 47. After the diagnosis I started noticing how most productivity tools assume consistent executive function which in turn is the exact thing ADHD disrupts. So I built something different.
DopaLoop is an iOS habit tracker that starts with goals ("better sleep", "less overwhelm") and lets you attach habits to them. Miss a day: nothing resets. The goal stays visible as an anchor or Northstar. The idea is that patterns over time matter more than daily streaks.
Tech: SwiftUI + SwiftData, with Foundation Framework and CoreML, fully local, no backend, no account. Privacy wasn't just a marketing decision, really. I just didn't want anyone to fear for their data, including myself or my kids. Everything stays on-device.
14-day free trial to get some momentum and gain insights from the analytics. No ads, no data collection.
Source isn't public, but happy to answer questions about the SwiftUI/SwiftData architecture, the HealthKit integration, or the ADHD-specific design decisions.
dopaloop.app (https://dopaloop.app/)
Best, Steviee
Show HN: Free open-source churn prediction for SaaS–Stripe and LLM interventions
ChurnGuard is an AI-powered platform that helps businesses reduce customer churn by predicting which customers are at risk of leaving and providing personalized retention strategies. The platform uses machine learning models to analyze customer data and identify patterns associated with churn, enabling companies to proactively address customer concerns and improve customer loyalty.
Show HN: Mcp2cli – One CLI for every API, 96-99% fewer tokens than native MCP
Every MCP server injects its full tool schemas into context on every turn — 30 tools costs ~3,600 tokens/turn whether the model uses them or not. Over 25 turns with 120 tools, that's 362,000 tokens just for schemas.
mcp2cli turns any MCP server or OpenAPI spec into a CLI at runtime. The LLM discovers tools on demand:
mcp2cli --mcp https://mcp.example.com/sse --list # ~16 tokens/tool
mcp2cli --mcp https://mcp.example.com/sse create-task --help # ~120 tokens, once
mcp2cli --mcp https://mcp.example.com/sse create-task --title "Fix bug"
Token savings are real, measured with cl100k_base: 96% for 30 tools over 15 turns, 99% for 120 tools over 25 turns.
It also ships as an installable skill for AI coding agents (Claude Code, Cursor, Codex): `npx skills add knowsuchagency/mcp2cli --skill mcp2cli`
Inspired by Kagan Yilmaz's CLI vs MCP analysis and CLIHub.
https://github.com/knowsuchagency/mcp2cli
Show HN: Dashboard for monitoring multiple Claude Code sessions
The article describes a code dashboard project that allows users to track and monitor their code repositories. The dashboard provides insights into code quality, build status, and other key metrics to help developers and project managers stay informed about the state of their codebase.
Show HN: Run 500B+ Parameter LLMs Locally on a Mac Mini
Hi HN, I built OpenGraviton, an open-source AI inference engine that pushes the limits of running extremely large LLMs on consumer hardware. By combining 1.58-bit ternary quantization, dynamic sparsity with Top-K pruning and MoE routing, and mmap-based layer streaming, OpenGraviton can run models far larger than your system RAM—even on a Mac Mini. Early benchmarks: TinyLlama-1.1B drops from ~2GB (FP16) to ~0.24GB with ternary quantization. At 140B scale, models that normally require ~280GB fit within ~35GB packed. Optimized for Apple Silicon with Metal + C++ tensor unpacking, plus speculative decoding for faster generation. Check benchmarks, architecture, and details here: https://opengraviton.github.io GitHub: https://github.com/opengraviton This project isn’t just about squeezing massive models onto tiny hardware—it’s about democratizing access to giant LLMs without cloud costs. Feedback, forks, and ideas are very welcome!
Show HN: OpenMeters – A fast and free audio metering/visualization suite
This has been a pet project of mine for the past ~5 months. It consists of six visualizations:
- Spectrogram: Implements the reassignment method for sharper time and frequency resolution. - Spectrum analyzer: A-weighted, frequency guidelines, loudest frequency tooltip. - Waveform: Colored based on frequency, loudness, or static - Oscilloscope: Tracks pitch and autocorrelates against a reference signal, provides stability. Also includes a regular zero-crossing trigger. - Stereometer & Phase meter: Linear and exponential scaling modes, adjustable windows. Multi-band correlation meter. - Loudness (LUFS & RMS): Implements the latest lufs standard. Adjustable timeframes.
Let me know what you think, and give it a star if you think it deserves as much. :] (check out the readme for a more complete enumeration of its features. Currently only available on Linux.)

Show HN: SimpleStats – Server-side Laravel analytics, immune to ad blockers
This article discusses how to implement server-side analytics tracking in a Laravel application. It covers key concepts like setting up a tracking event system, storing user events in a database, and visualizing the data using charts and graphs.

Show HN: I built a database of air fry times for 300+ foods
The article provides a comprehensive overview of air fryers, including their features, benefits, and top models on the market. It offers guidance on choosing the right air fryer for your needs and provides tips for using it effectively.
Show HN: ANSI-Saver – A macOS Screensaver
Hi, I've been working on something I've been thinking for long time but since I had no experience with macOS screen savers I always posponed. Now thanks to Claude I was able to create a screensaver that scroll ANSI files while your computer is idle.
It allow to use local ANS files or packs directly from 16colo.rs.
Repo: https://github.com/lardissone/ansi-saver

Show HN: MindfulClaude – Guided breathing during Claude Code's thinking time
Every time Claude Code thinks, you get 10-60s of idle time, usually spent on context switching or doomscrolling. I turned it into breathing exercises that keep you focused and improve your heart rate variability.
Auto-launches a tmux pane using hooks when Claude starts working and disappears when it finishes.
Show HN: Colchis Log – cryptographic audit trail for AI systems (Python)
Built a tamper-proof execution logging library for AI systems.
SHA-256 hash chain detects any tampering. Content-addressable payload store. CLI + Web interface. Works fully offline.
Ko-fi: https://ko-fi.com/s/50fccfeecd
Show HN: Ratschn – A local Mac dictation app built with Rust, Tauri and CoreML
Hi HN, I'm the solo developer behind Ratschn.
I type a lot and got extremely frustrated with the current state of Mac dictation tools. Most of them are either heavy Electron wrappers, rely on cloud APIs (a privacy nightmare), or force you into a SaaS subscription for a tool that essentially runs on your own hardware. I wanted something that feels native, respects system resources, and runs entirely offline without forced subscriptions.
The stack is Rust, Tauri, and whisper.cpp. Here are the design decisions I made:
Model Size vs. Accuracy: Instead of using the smallest possible model just to claim a tiny footprint, the app downloads a ~490MB multi-language Whisper model locally on the first run. I found this to be the sweet spot for high accuracy (accents, technical jargon) to drastically reduce text correction time.
Hardware Acceleration: The downloaded model is compiled via CoreML. This allows the transcription to run directly on the Apple Neural Engine (ANE) and Metal on M-series chips, keeping the main CPU largely idle.
Memory Footprint: By using Tauri instead of Electron, the UI footprint is negligible. While actively running, the app takes up around 500MB of RAM. This makes perfect technical sense, as it is almost entirely the ~490MB AI model being actively held in memory to ensure instant transcription the millisecond you hit the global shortcut.
Input Method: It uses macOS accessibility APIs to type directly into your active window.
Business Model & Pricing: I strongly dislike subscription fatigue for local tools. There is a fully functional 7-day free trial (no account required). If you want to keep it, my main focus is a fair one-time purchase (€125 for a lifetime license). However, since I highly value the technical feedback from this community, I generated an exclusive launch code (HN25) that takes 25% off at checkout (dropping it to roughly €93 / ~$100).
Bug Bounty: Since I'm a solo dev, I know I might have missed some edge cases (especially around CoreML compilation on specific M-chips or weird keyboard layouts). If you find a genuine, reproducible bug and take the time to report it here in the thread, I will happily manually upgrade you to a free Lifetime license as a massive thank you for the QA help.
I'd love to hear your technical feedback on the Rust/Tauri architecture or how the CoreML compilation performs on your specific Apple Silicon setup. Happy to answer any questions!