
Two Years of Emacs Solo
This article chronicles the author's two-year journey of using Emacs as their sole text editor, highlighting the benefits they've experienced, such as increased productivity, customizability, and a deeper understanding of their computing environment.

No, it doesn't cost Anthropic $5k per Claude Code user
The article debunks the claim that it costs Anthropic $5,000 per user to provide access to the Claude AI, explaining that the actual costs are significantly lower and that the company's pricing is based on various factors, not a fixed per-user cost.

Learnings from paying artists royalties for AI-generated art
The article discusses Kapwing's experience with paying royalties to artists whose work was used to train their AI model, highlighting the challenges and lessons learned in establishing a fair and sustainable model for compensating creators in the AI-generated art ecosystem.

Rendezvous with Rama
The article discusses the science fiction novel 'Rendezvous with Rama' by Arthur C. Clarke. It explores the novel's premise of a mysterious alien spacecraft entering the Solar System and the scientific and philosophical implications of such an encounter.

The first airplane fatality
The article recounts the tragic story of Thomas Selfridge, the first person to die in an airplane accident. Selfridge was a passenger on a demonstration flight with Orville Wright in 1908 when the plane crashed, leading to Selfridge's death and the recognition of the need for improved aircraft safety measures.

Windows: Microsoft broke the only thing that mattered
Microsoft has made significant changes to its Windows operating system, which has sparked controversy among users. The article discusses the company's decision to prioritize new features and design elements over the core user experience that many have come to rely on.

The “JVG algorithm” only wins on tiny numbers
The article discusses the author's perspective on the concept of quantum supremacy, its implications for the future of quantum computing, and the challenges involved in achieving and verifying this milestone.

Amazon holds engineering meeting following AI-related outages
The article discusses the potential impact of artificial intelligence (AI) on the legal profession, highlighting concerns about AI's ability to automate certain legal tasks and the ethical challenges it poses in the field of law.
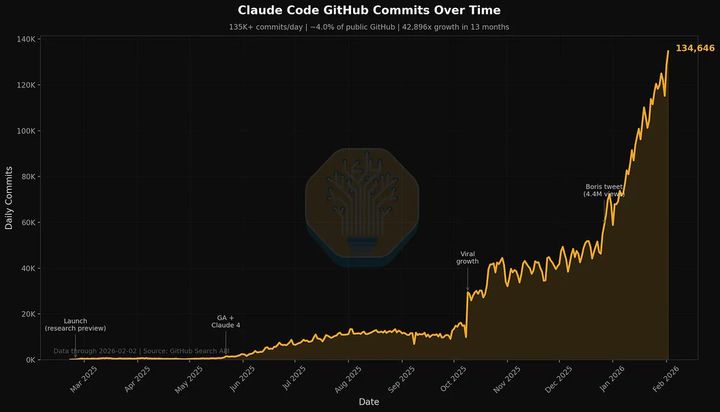
Claude Code, Claude Cowork and Codex #5
This article discusses the author's experience with Claude, an AI assistant, and its potential to revolutionize work and collaboration through features like code writing, task completion, and knowledge retrieval.

Iran's attacks on Amazon data centers in UAE, Bahrain signal a new kind of war
Iran's recent cyberattacks on Amazon data centers in the UAE and Bahrain mark a new era of warfare, as AI technology plays an increasingly strategic role, according to analysts. These attacks demonstrate the growing threat of state-sponsored cyber warfare targeting critical infrastructure.

US blindsides states with surprise settlement in Live Nation/Ticketmaster trial
The U.S. government has reached a surprise settlement in its antitrust lawsuit against Live Nation and Ticketmaster, ending the trial before its conclusion. The settlement allows the companies to continue their merger and maintain their dominant position in the live music ticketing industry.

The Cost of 'Lightweight' Frameworks: From Tauri to Native Rust
The article discusses the author's dislike for WebKit and their reasons for preferring other web rendering engines. It outlines technical issues the author has encountered with WebKit and advocates for more competition in the browser engine market.

60 Minutes Havana Syndrome report finds U.S. government tested energy weapon
The article reports that a U.S. government investigation has found evidence that the mysterious 'Havana Syndrome' afflicting diplomats and intelligence officers may have been caused by the testing of an energy weapon. The article explores the details of this investigation and the potential implications of these findings.

United States Leads Dismantlement of One of the Largest Hacker Forums
The United States Department of Justice announced the dismantling of one of the world's largest hacker forums, RaidForums, which was used to facilitate the buying and selling of stolen sensitive information and hacking tools.
Spotify announce plans to limit Development Mode
Spotify is updating its developer access and platform security policies to enhance user privacy and platform integrity. The changes include new requirements for app developers, increased authentication measures, and expanded data restrictions to ensure a secure and trustworthy experience for Spotify users.
Kettle, open source tooling for TEE-attested builds
The article introduces Kettle, an open-source data integration tool that allows users to extract, transform, and load data from various sources. Kettle provides a user-friendly graphical interface and supports a wide range of data sources, making it a versatile tool for data integration and management tasks.

Concern over US travel visas prompts Ig Nobels to move its awards to Europe
The article discusses the 2022 Ig Nobel Prizes, which honor comical scientific achievements that first make people laugh, then make them think. The prizes were awarded for research on topics such as the unexpected benefits of using a metronome while walking, the physics of partially full beer bottles, and the applications of vortex-induced vibrations.

Open Weights Isn't Open Training
The article discusses the concept of open weights and open training, which involves making the underlying weights and models of AI systems publicly available. This approach aims to promote transparency, collaboration, and the advancement of AI technology.

Trump considering taking over Strait of Hormuz
The article discusses President Trump's comments on the ongoing tensions between the U.S. and Iran, particularly regarding the situation in the Strait of Hormuz. It highlights the president's assertion that the 'war is very complete' and provides context around the current state of the conflict.
Press-One: Auto-accept every Claude Code prompt
The article discusses the development of Press One, an open-source, decentralized social media platform that aims to provide users with more control over their data and content. It highlights the platform's focus on privacy, content moderation, and the use of blockchain technology to ensure transparency and user empowerment.